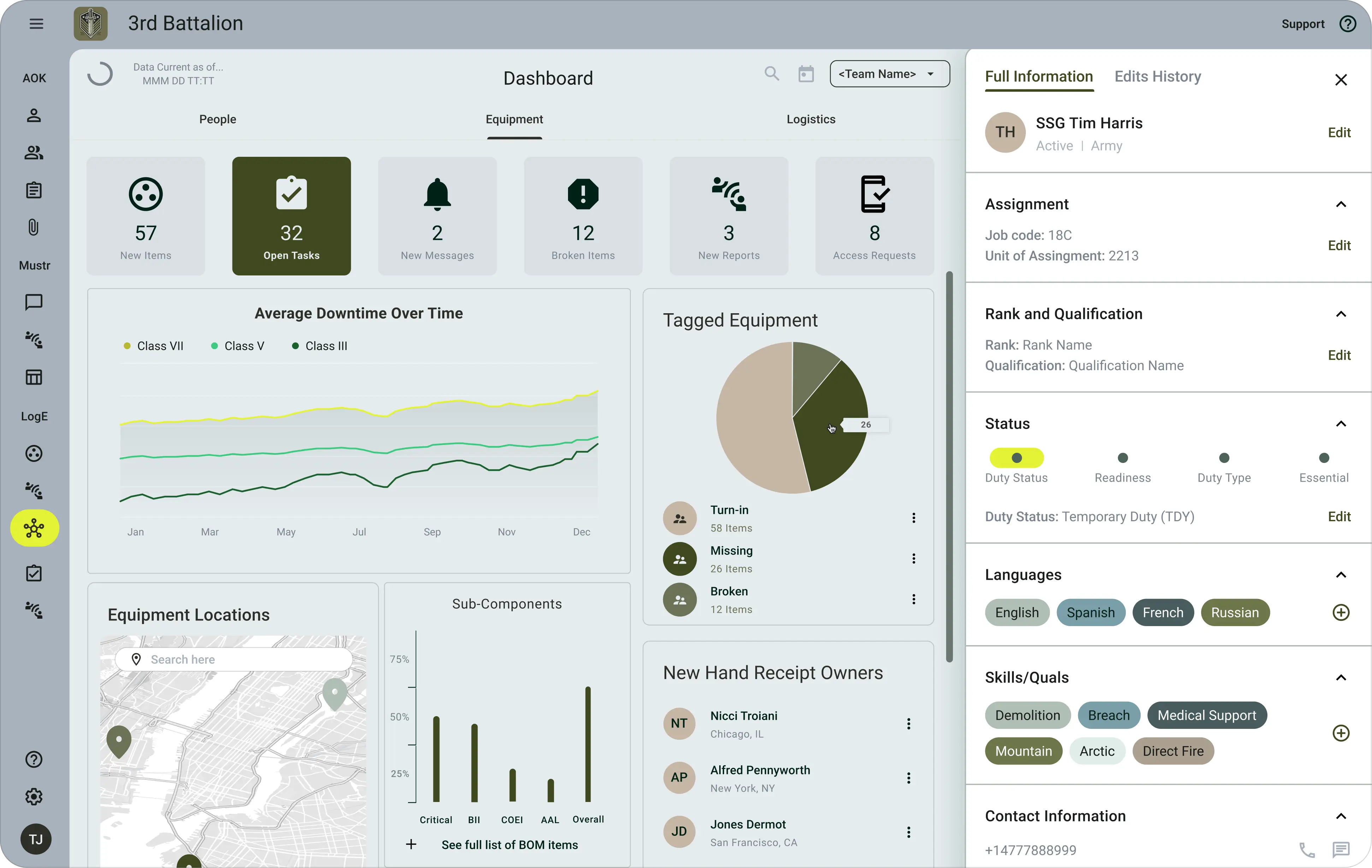
The Adyton Solutions Platform (ASP) is a combination of Adyton’s user-facing applications — The Adyton Operations Kit — and our proprietary backend tech stack, which we call The Adyton Operations Core.
The truth is that we’re throwing a lot of terms at you. And, in order to securely deploy mobile-first technology on any government-issued or personal device with America’s warfighters, it requires a lot of engineering work users don’t often see.
To that end, we’re using this space to explain how the Adyton Solutions Platform, The Adyton Operations Kit, and The Adyton Operations Core work and interact with one another.
The Adyton Solutions Platform
Fundamentally, the Adyton Solutions Platform performs three primary functions:
- Ingest and transform: The Adyton Operations Core (AOC) turns raw information into curated, enriched data that feeds our data models, enabling consistent structure and meaning across data assets.
- Access and interact: Users access data through the Adyton Operations Kit (AOK), a suite of mobile defense products built for the warfighter that digitizes and automates operational processes. AOK can be used on personal or government issued devices, enabling members of our military to view, update, and interact with operational data in real-time wherever they are, including offline and D3 environments.
- Generate and enrich: As users interact with the AOK, they create new, immediately structured data and audit trails — photos, status updates, quality, quantity, and location assessments — that enhance the value and utility of AOK's dataset for users and enterprise AI systems that connect to ASP through AOC.
Let’s dive into the component parts.
The Adyton Operations Kit
The soldiers, sailors, airmen, Marines, and guardians that use Adyton products are using The Adyton Operations Kit (AOK), which is the user-facing aspect of ASP. AOK is a suite of three mobile defense products — with more to come — that does two things:
For the individual warfighter, we’re improving their quality of life, reducing time spent on administrative work for processes like scheduling, leave requests and unit transfers, and saving their time by digitizing and automating equipment and munitions management.
For military leadership, we’re generating net new, real-time data about personnel, equipment, and munitions from the edge up through the chain of command to increase the readiness, operational agility, and lethality of America’s forces.
The three applications in AOK are Mustr, Log-E, and Skeds.
Mustr is designed for personnel management, accountability, and structured communications. Leaders use Mustr to send structured communications to their team, such as requests for information and announcements. Recipients can access communications and files securely via the AOK app or text. At its most basic, Mustr enables instantaneous, secure communications to configurable groups of individuals under an individual’s command — replacing email, Signal, or physical bulletin boards with a digital system.
Log-E is built for real-time equipment and munitions status and distributed logistics. Members of the Army use Log-E to track equipment and munitions digitally, replacing the paper hand receipt. Leadership can find where equipment is located, who’s using it, and what condition it’s in across the entire force and automate team-wide reports to obtain an aggregate view of pertinent equipment and munitions. Not only does Log-E save troops time, but it provides complete visibility of readiness for distributed forces with an accurate view of current stock status, on-hand quantities, and potential future requirements, reducing emergency supply needs and enabling smarter purchasing decisions at the enterprise level.
Skeds, in beta, is our smart scheduling application for mission-ready teams. Rather than spreadsheets or whiteboards, teams can manage schedules of their team digitally from any device. It’s one view for all activities for personnel, from doctor’s appointments to deployments. It can be integrated into enterprise applications like ATIS or Office 365, connecting personnel in the field to those in HQ. With Skeds, manual and disparate schedules across calendars are a thing of the past.
The Adyton Operations Core
The Adyton Operations Core (AOC) is ASP’s back end — our proprietary tech stack. We don’t have enough time to detail all the underlying technologies, but there are a few components, or layers, that are critical to building secure and trusted mobile technology our military can rely on.
Identity layer: When a user is logging munitions or communicating with their team, users need to trust that the person doing the action is in fact, that person. AOC has Decentralized Identity and Distributed Authorization features, along with zero-trust architecture that eliminates implicit trust and continuously validates every stage of a digital interaction. Our technology can also integrate with the existing identity management solutions. The long and the short of it is, you can trust who’s using AOK at every interaction.
Permissions layer: We know that not every user needs to see every single piece of information. At the same time, unwieldy and inflexible permissioning provisions can make technology functionally unusable. To solve for this, we provide data granularly, down to the atomic data element level. This means that only authorized personnel can access specified information based on strict, pre-defined permissions.
Semantic layer: Our semantic layer is, in many ways, our secret ingredient. It defines shared concepts and relationships (e.g., personnel, equipment, missions, locations) across all applications in the Adyton Operations Kit. Unifying data — ensuring it all speaks the same language — is what enables workflows across AOK applications and the AI-driven functionality we’re building like unified search and cross-linking between people, tasks, equipment.
Our semantic layer is also critical to data sharing across companies or units or battalions, as well as entire branches of the DOD, and even between U.S. and allied forces. Unlike similar technologies, our semantic layer is lightweight and edge-compatible, so it doesn’t require a ton of infrastructure to deploy and use.
Data sync layer: The Data Sync Layer makes the Adyton Solutions Platform truly offline-first. Every action in the Adyton Operations Kit — from logging gear in Log-E to sending a Mustr message and updating schedules in Skeds — is stored locally and syncs seamlessly when connectivity returns. Using CRDT-backed storage, peer-to-peer mesh networking (Bluetooth/Wi-Fi), and domain-aware merge rules, our system ensures that data stays consistent, auditable, and secure even in degraded, denied, or disconnected (D3) environments. When devices reconnect, updates flow back into the Adyton Operations Core’s secure backend, preserving permissions and audit trails. Our data sync layer ensures warfighters never need to think about signal strength — their tools simply work wherever they are in the world.
Empowering the warfighter
Every minute of every day, the entire Adyton team is focused on making the people who protect us more ready, resilient, and responsive.
When U.S. servicemembers spend less time on administrative tasks and paperwork, they’re more effective in the garrison environment because they’re spending more time at the range and preparing for their mission. This makes every single warfighter more lethal and safer when they’re deployed to the battlespace.
Investing in underlying technologies that keep data protected and enable warfighters and leadership alike to coordinate mission critical personnel deployments and equipment resupply across divisions, branches, and even between allied forces and the U.S. military — anywhere in the world — ensures combat readiness.
When the U.S. military shifts from pen and paper to flexible ones and zeroes using ASP, we’ll help every single man and woman serving our country be at their best.
If this sounds like something you’d be interested in helping build, join our team.
.png)